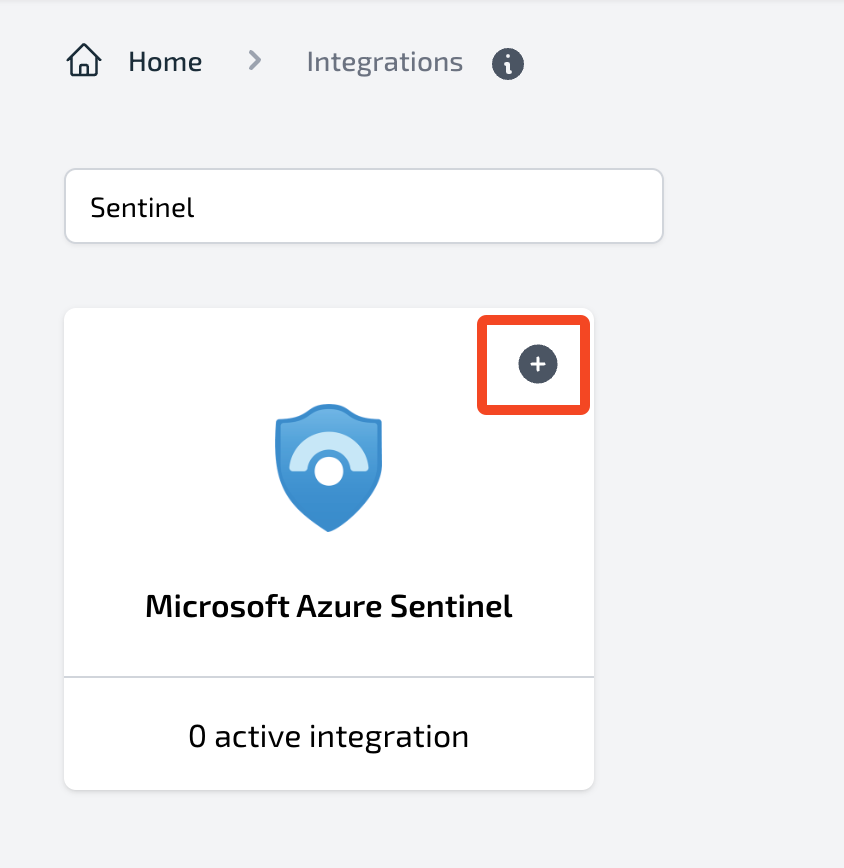
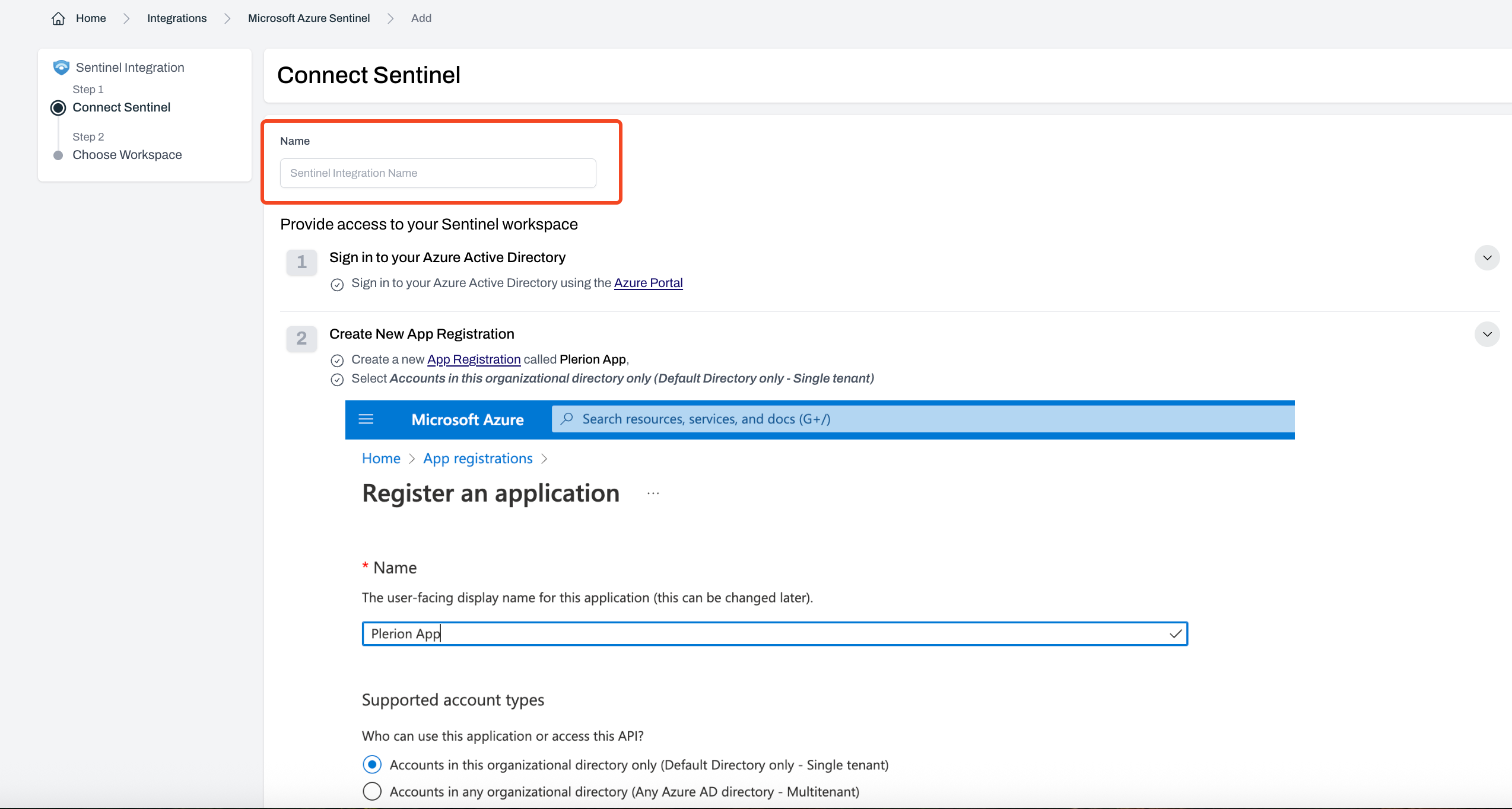
Steps to integrate Microsoft Sentinel with Plerion
Enter your Microsoft Azure credentials
Provide the following details from your Azure environment: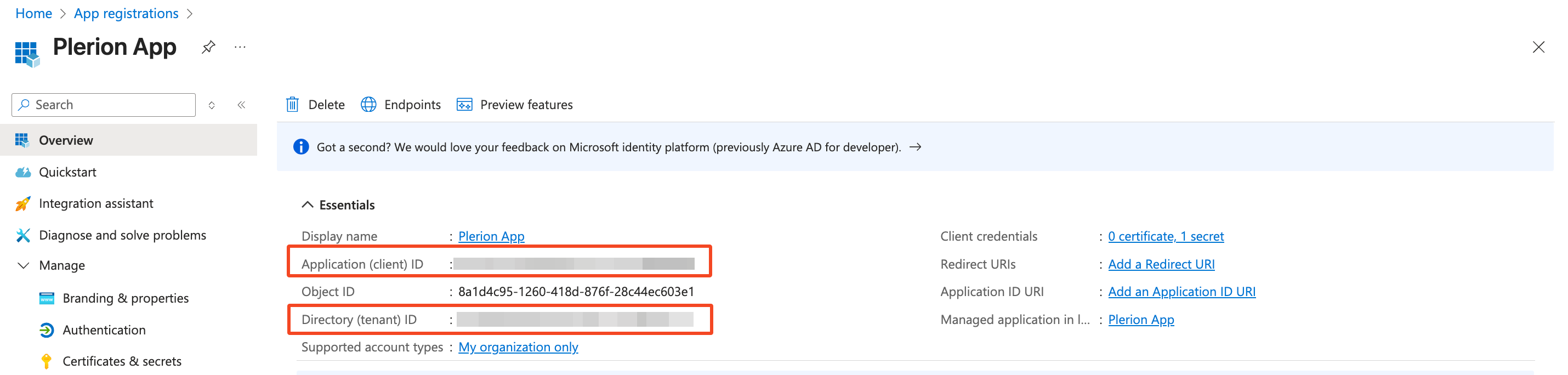
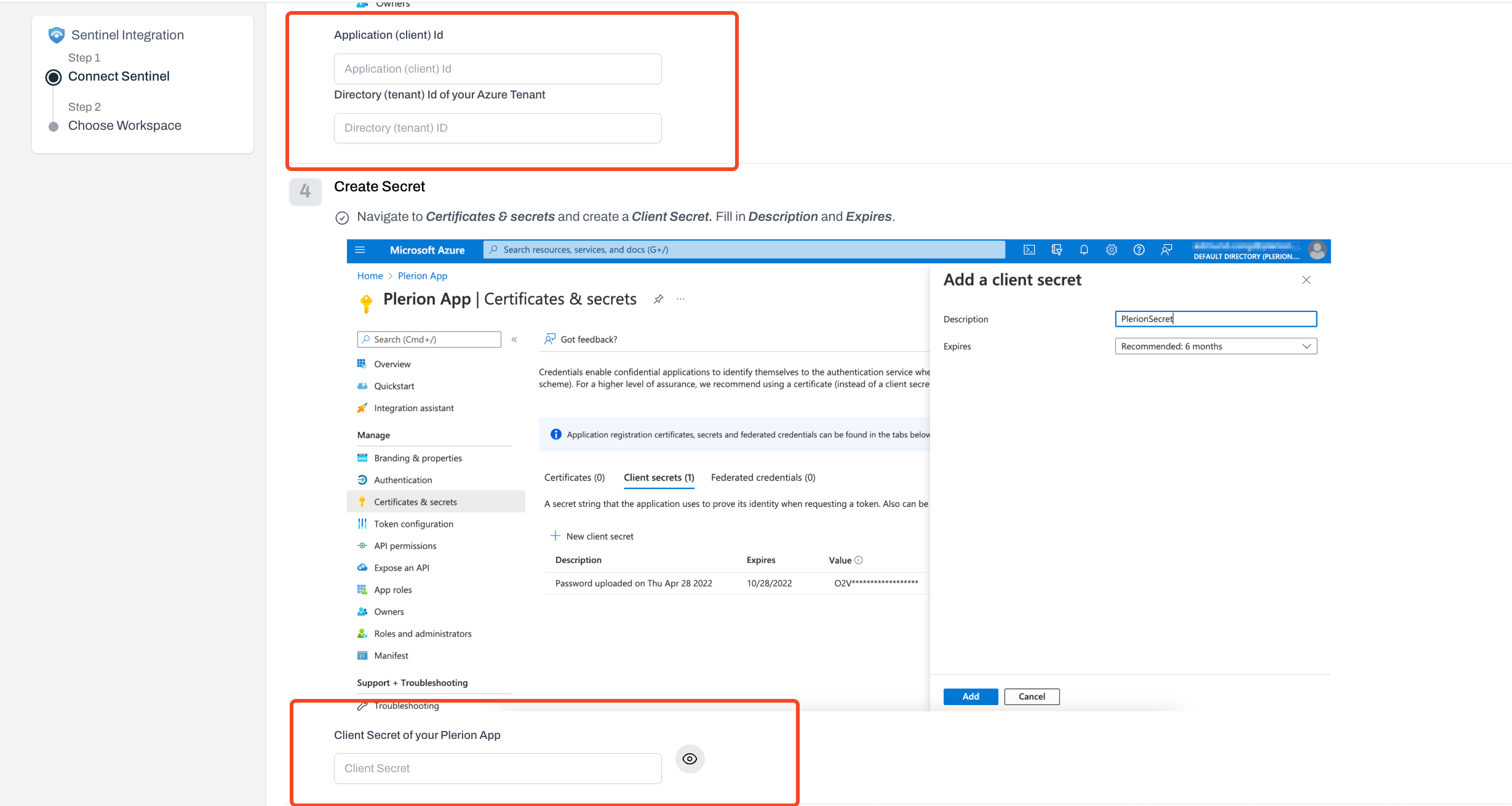
- Application ID
- Directory ID
- Client Secret
- Subscription ID
Next.

Choose your Sentinel workspace settings
Select the workspace, resource group for Plerion alerts created in Sentinel.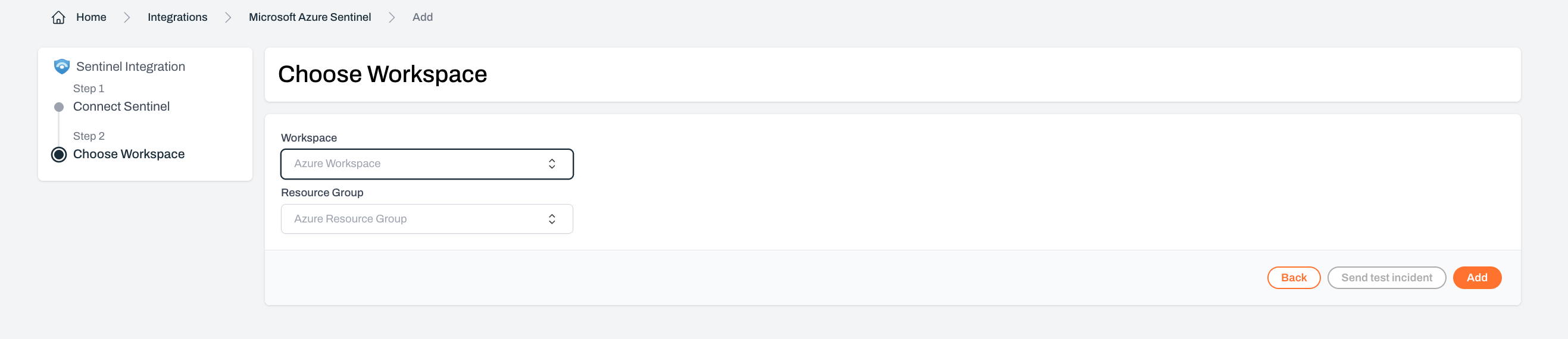

Test your Microsoft Sentinel integration
Click 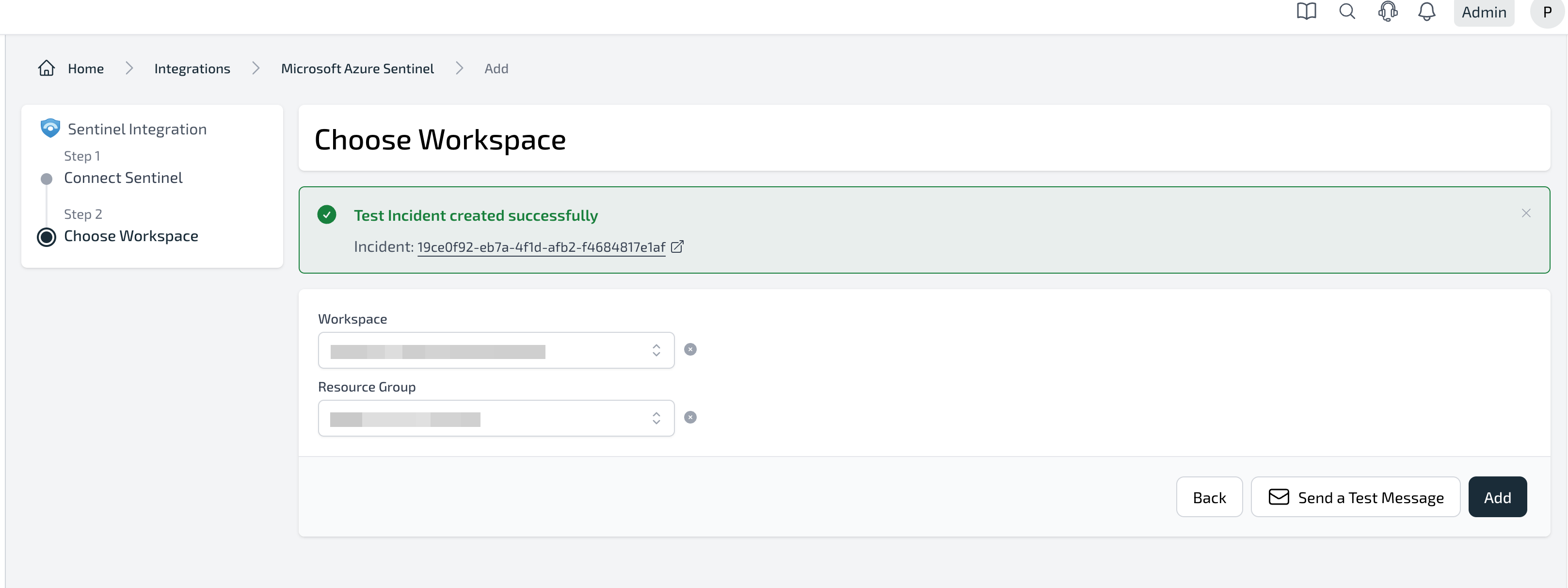
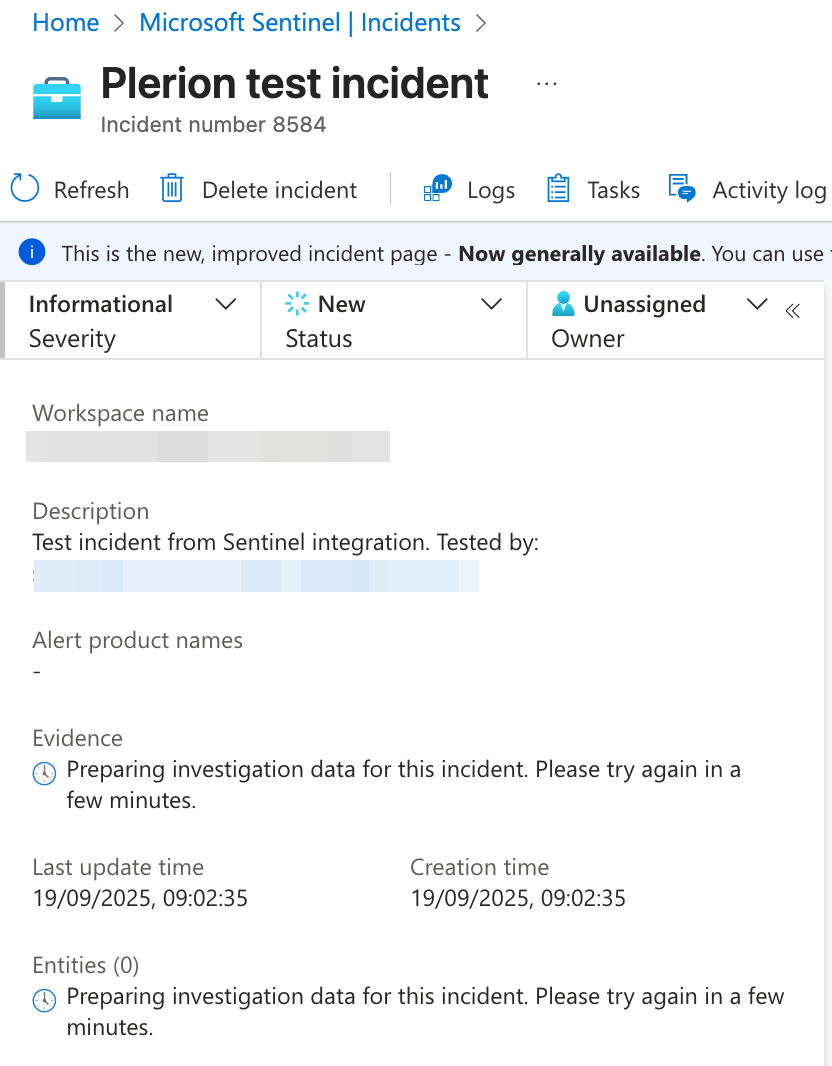
Send test message to confirm the configuration. A test incident will be created in your chosen Sentinel workspace.