Default workflow
Plerion includes a default workflow that is already configured to detect and alert on high-risk scenarios:- Assets that are publicly exposed
- Assets with a risk score greater than or equal to 9
- Findings where potential attack paths have been identified
Third-party integrations
You can set up workflows with the following third-party tools:- ClickUp
- Drata
- Jira and Jira Security
- Linear
- Microsoft Teams
- PagerDuty
- ServiceNow
- Slack
- Vanta
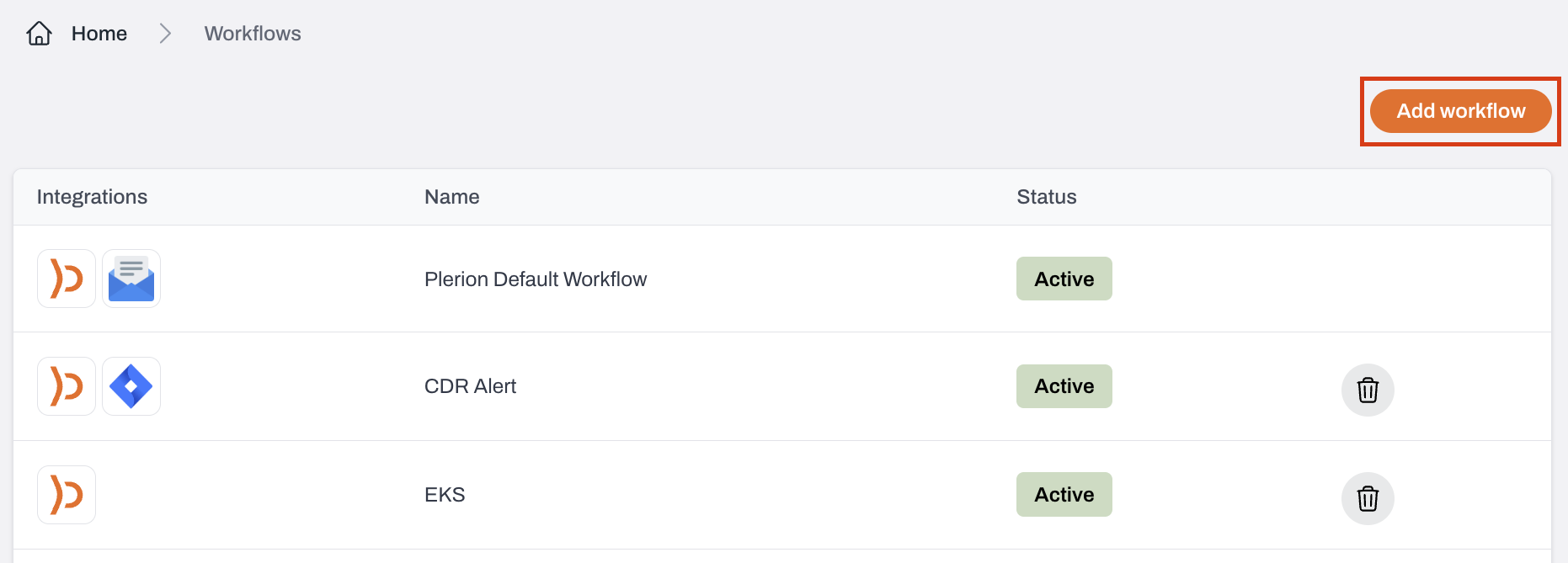
Steps to create a new workflow
Enter a name and description
Turn on the Enabled toggle to activate the workflow and start receiving alerts.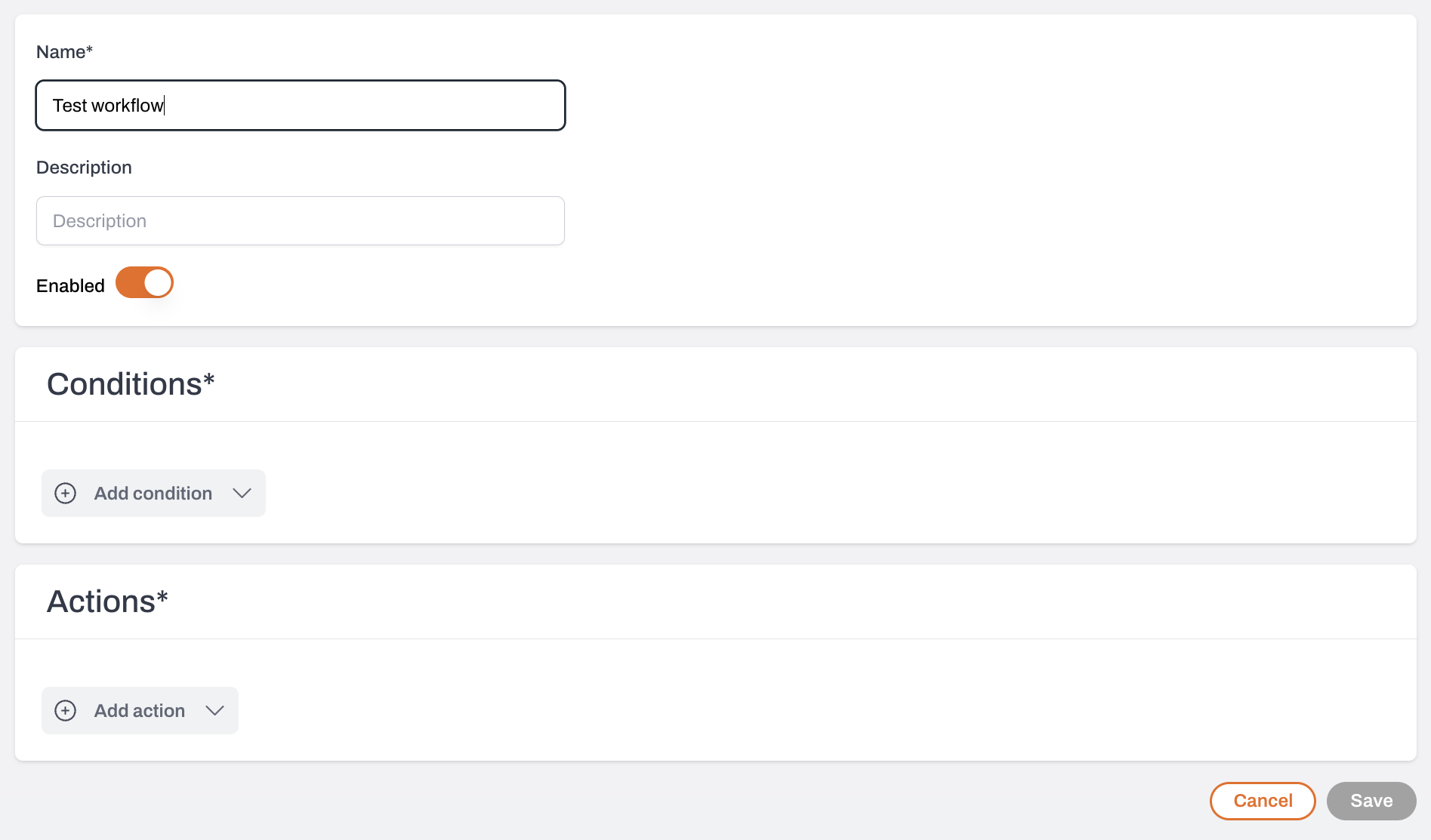

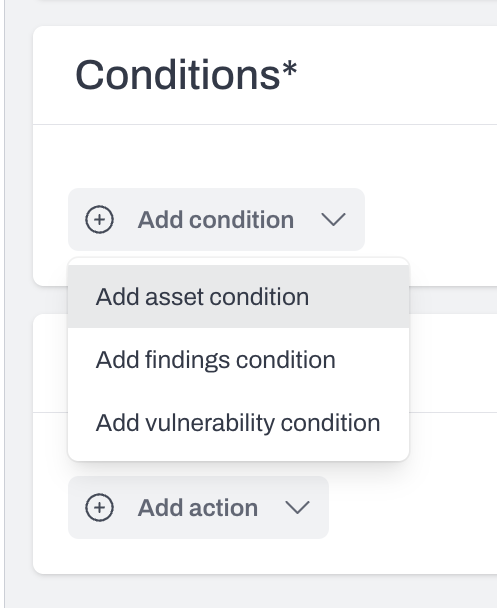
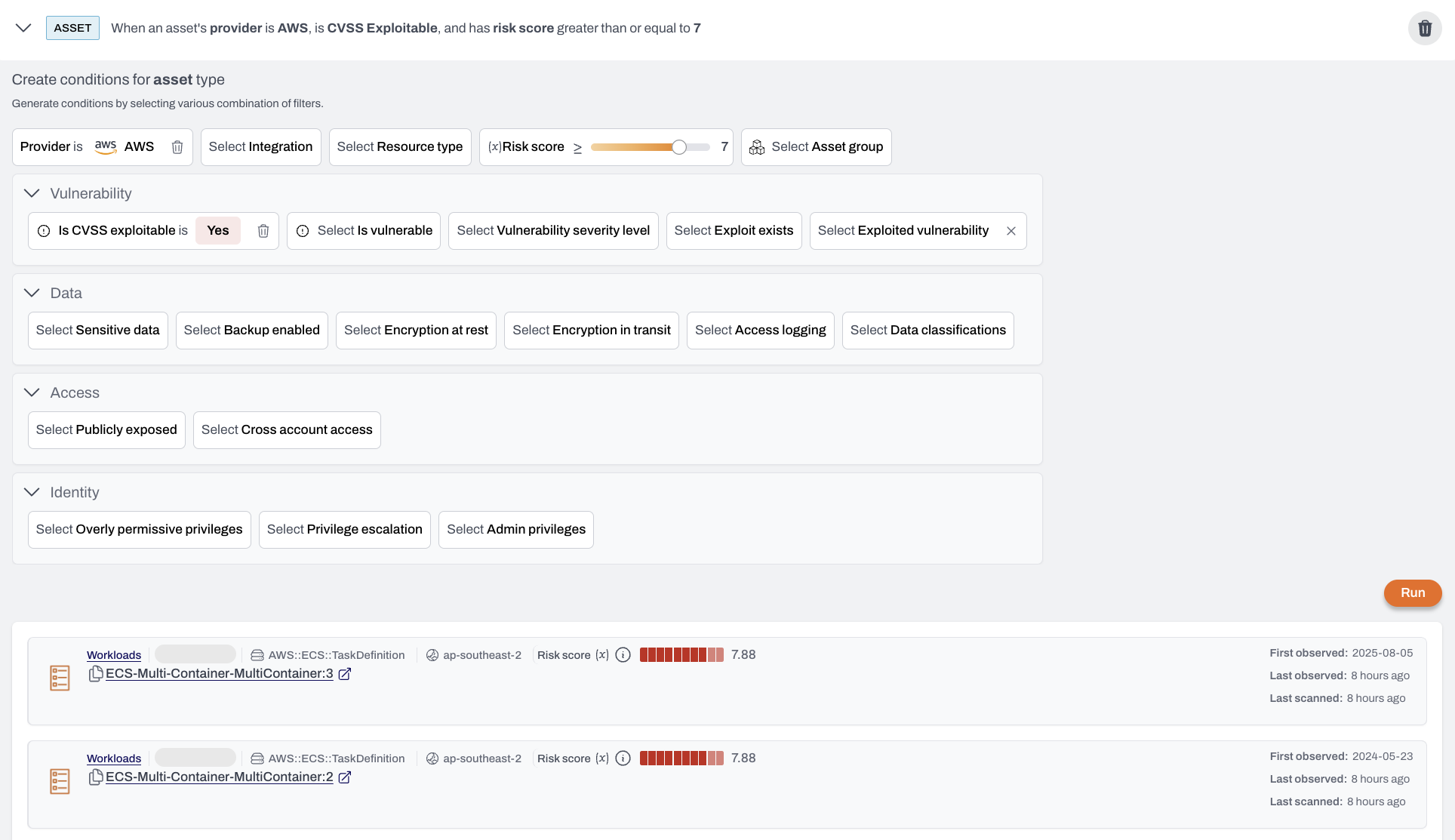
Define your conditions
- Add conditions for assets, findings, or vulnerabilities.
- When multiple conditions are added, Plerion applies OR logic.
- Click
Runto preview results that match your conditions.
Select where alerts should be delivered
Alerts that match the defined conditions will appear in your Plerion alerts dashboard and can also be sent to configured third-party integrations.